Lab: SQL injection attack, querying the database type and version on MySQL and Microsoft | Web Security Academy
PortSwigger: SQL injection attack, querying the database type and version on MySQL and Microsoft | System Weakness
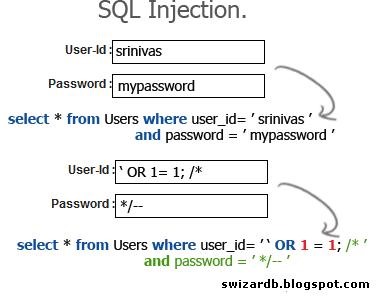
The Essential Newbie's Guide to SQL Injections and Manipulating Data in a MySQL Database « Null Byte :: WonderHowTo

Lab: SQL injection attack, querying the database type and version on MySQL and Microsoft | Web Security Academy
![A Deep Dive into Database Attacks [Part IV]: Delivery and Execution of Malicious Executables through SQL commands (MySQL) A Deep Dive into Database Attacks [Part IV]: Delivery and Execution of Malicious Executables through SQL commands (MySQL)](https://www.imperva.com/blog/wp-content/uploads/sites/9/2018/03/Screen-Shot-2018-03-14-at-3.17.51-PM.png)